Overcoming Compliance Confusion: Why You Need a SOC 2 Foundation

Yes, it’s overwhelming.
There is a rising wave of formal compliance efforts today, driven by customer demands, regulatory requirements, and/or the organizations’ desires to demonstrate its internal security controls and practices to external parties. Recent data protection laws have enshrined the individual’s right to privacy and security of their personal data across the globe. As personal information only becomes more valuable, the frequency and severity of security breaches accelerates. Organizations that fail to adequately secure their data face potentially devastating fines and loss of reputation.
The question often comes up regarding which compliance commitment is the right one for an organization to pursue. There are regulations at various levels of government that define the protection of data and prescribe serious penalties for non-compliance. Among many, there are some well known examples:
– In the United States, HIPAA requires that healthcare organizations protect the privacy of patients’ medical records and information.
– In Canada, PIPEDA governs how private sector organizations collect, use, and disclose personal information in the course of commercial business.
– Internationally, PCI DSS is a specific standard regarding the protection of payment cardholder data.
– In the European Union, GDPR legislation prescribes data protection and privacy for all individuals within the European Union centering around the individual’s right to be forgotten. Fines can be up to 4% of total annual revenue for non-compliance.
With so many regulations, standards, and certifications, it’s no wonder that businesses are confused. Industry standards and approaches have evolved to better protect the data they handle, yet their variety and complexity can leave you struggling to know where to begin. While most have specific and unique requirements, all require a common set of best practices with respect to privacy and the protection of data and service. Using a well known standard (e.g. SOC 2 report) or certification (e.g. ISO 27001) to establish a solid foundation for information security will help your organization keep up with the evolving demands of compliance.
Establishing the Foundation
As leading standards, SOC 2 and ISO 27001 can present organizations with significant advantages over market competition by demonstrating the design and operating effectiveness of internal controls. ISO 27001 is a framework of standards that help businesses implement a solid Information Security Management Management System (ISMS). SOC 2 is a set of criteria and controls that measure how organizations handle areas related to the security, availability, processing integrity, confidentiality, privacy of a system, or a given subsets of those areas. While the regulations you need to follow will depend on your industry, customer base, region, and market, there are enough overlapping requirements between established standards and various regulations that make either SOC 2 or ISO 27001 good foundations.
SOC 2 and ISO 27001 were developed to mitigate similar risks, and they are both assessed by third-party auditors to provide independent assurance that the controls in place meet the necessary criteria. The criteria/controls bear similarities in many areas:
– Risk management
– Delineation and understanding of responsibilities, including InfoSec roles and responsibilities, operational planning and control, and leadership and commitment
– Policy and procedure implementation for information security
– Logical and physical security controls
– Password management protocols
See the table below for a high-level comparison.
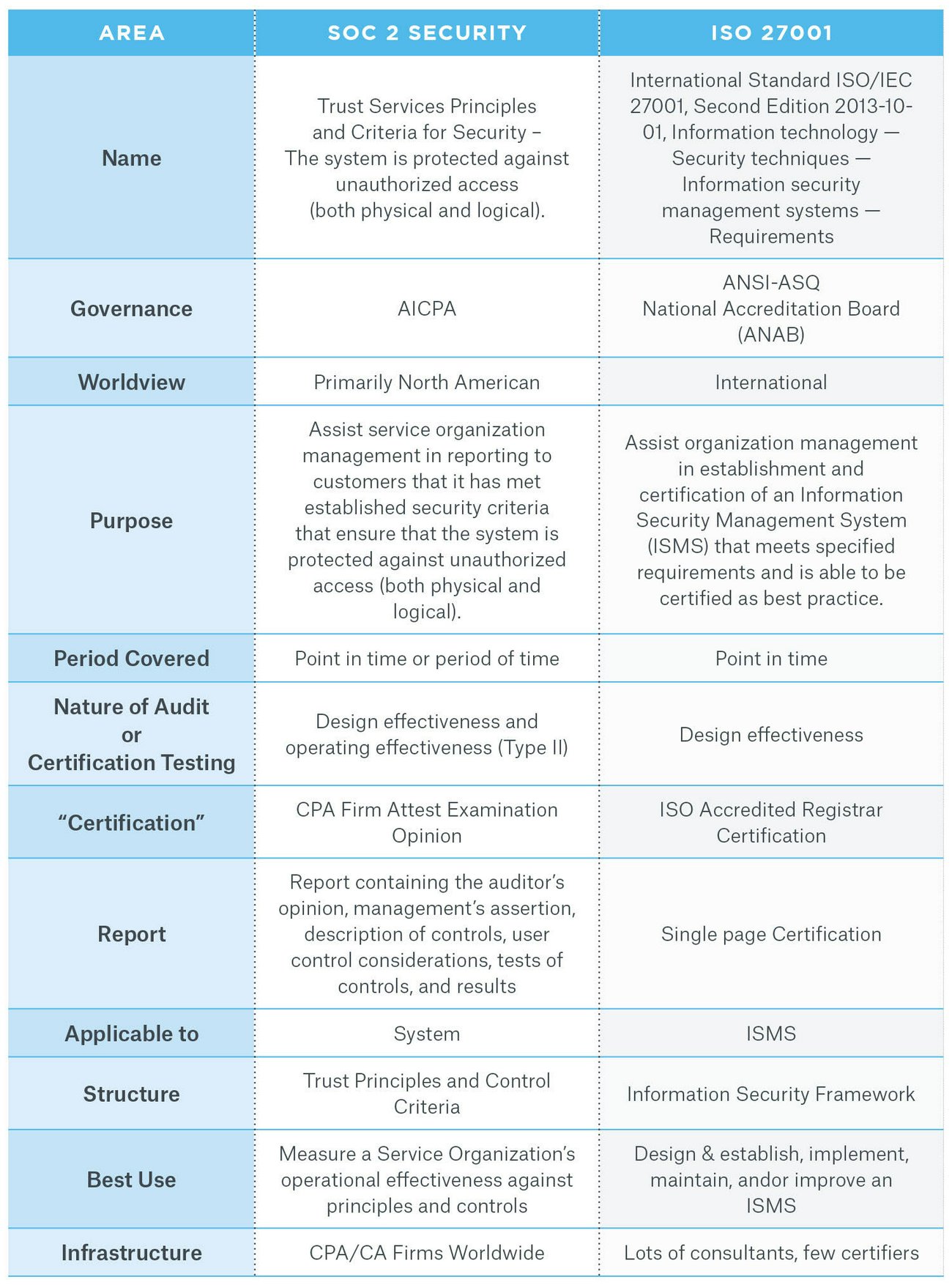
The AICPA has shared a detailed mapping of the 2014 Trust Services Criteria to 2013 ISO 27001, which can be downloaded here.
Simplifying Compliance Efforts
The bottom line is that you have to choose the standard that is best suited to your market and customers, so select one that will align you with practices that bring you closer to meeting another standard. Importantly, because the SOC 2 Type 2 audit covers a six month span, SOC 2 goes farther than ISO 27001 in that in addition to design it measures operating effectiveness over time. SOC 2 is also a leading standard in North America and, for the purposes of this post, will be used as the reference basis for creating a solid foundation to leverage.
A SOC 2 compliant foundation will simplify the effort required to achieve and demonstrate compliance with various regulations, and make positive results more predictable. With an attestation that SOC 2 controls are in place and adhered to on a regular basis, your organization can gain comfort knowing that it is well positioned to satisfy a range of demands. For example, while the same exercise can be done for other regulations–like for HIPAA–if you are wondering how far SOC 2 or ISO 27001 will get you on the GDPR, which comes into effect later this month on May 25, we have generated a very high-level mapping below to illustrate coverage levels on critical elements.
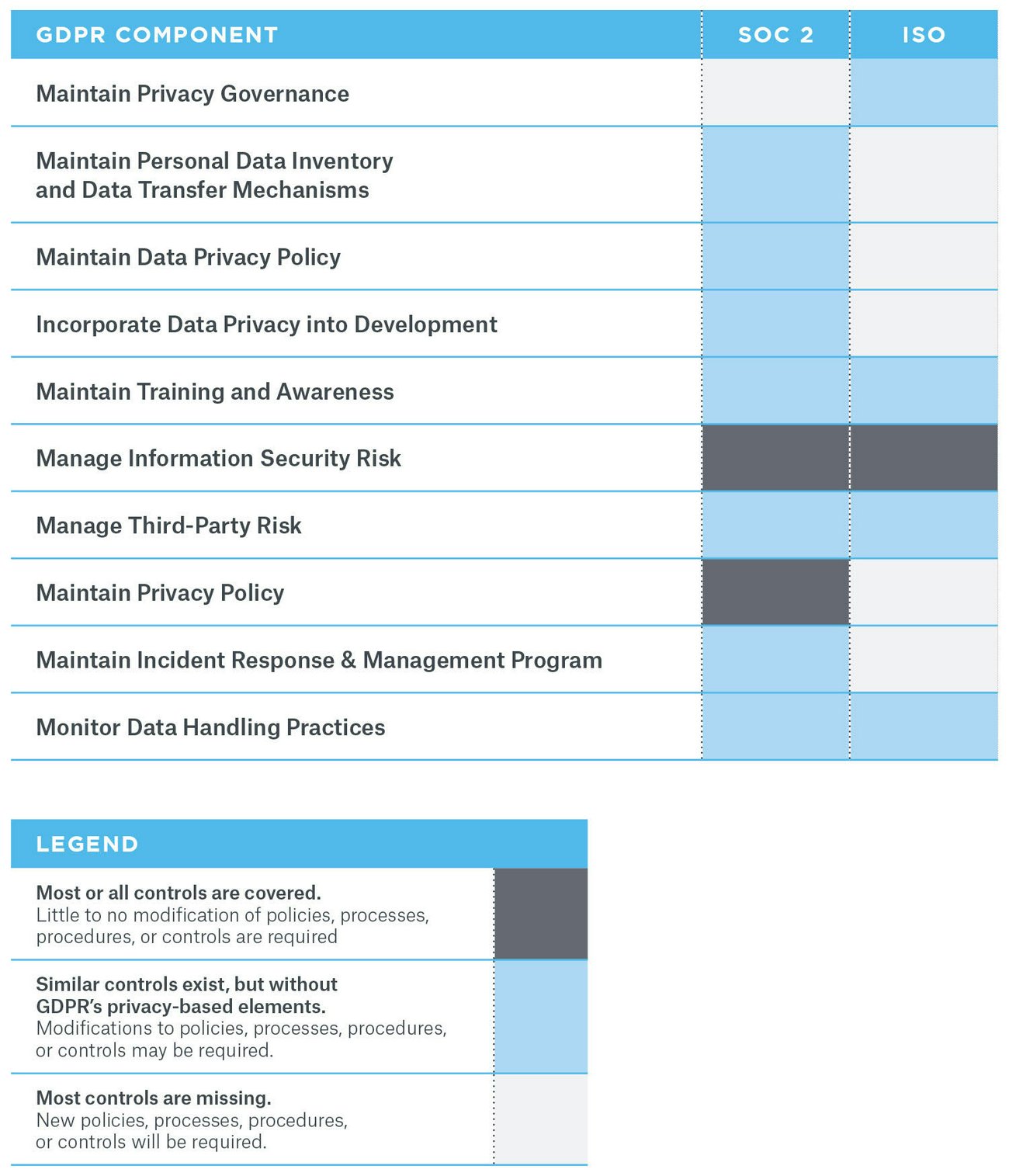
Reducing Risk
If you are looking to move to the cloud, it is important that your application is ready to face evolving compliance requirements. A good place to start is to work with a cloud provider that has proven good practices, like a SOC 2 attestation report. This will enable part of your operations to come with ‘built-in’ security and security practices, and it will reduce the scope of work required of your team to align its own information security practices. Furthermore, having an application platform layer that is SOC 2 compliant will streamline the security practices from the cloud provider into the application layer, and this will help prevent risks and vulnerabilities from seeping into your application layer. Ultimately, this will simplify your efforts to achieve SOC 2 compliance for your entire application environment and surrounding processes, and make it easier to comply with applicable standards, certifications, and/or regulations
CloudOps’ Services
CloudOps can help organizations’ production systems become SOC 2 compliant. By leveraging CloudOps’ Managed Application Platform (MAP) offering and expertise, your application platform layer could benefit from good practices aligned with SOC 2 criteria and controls. Below is a view of many tasks CloudOps’ services would manage, covering much of your organization’s SOC 2 compliance scope.
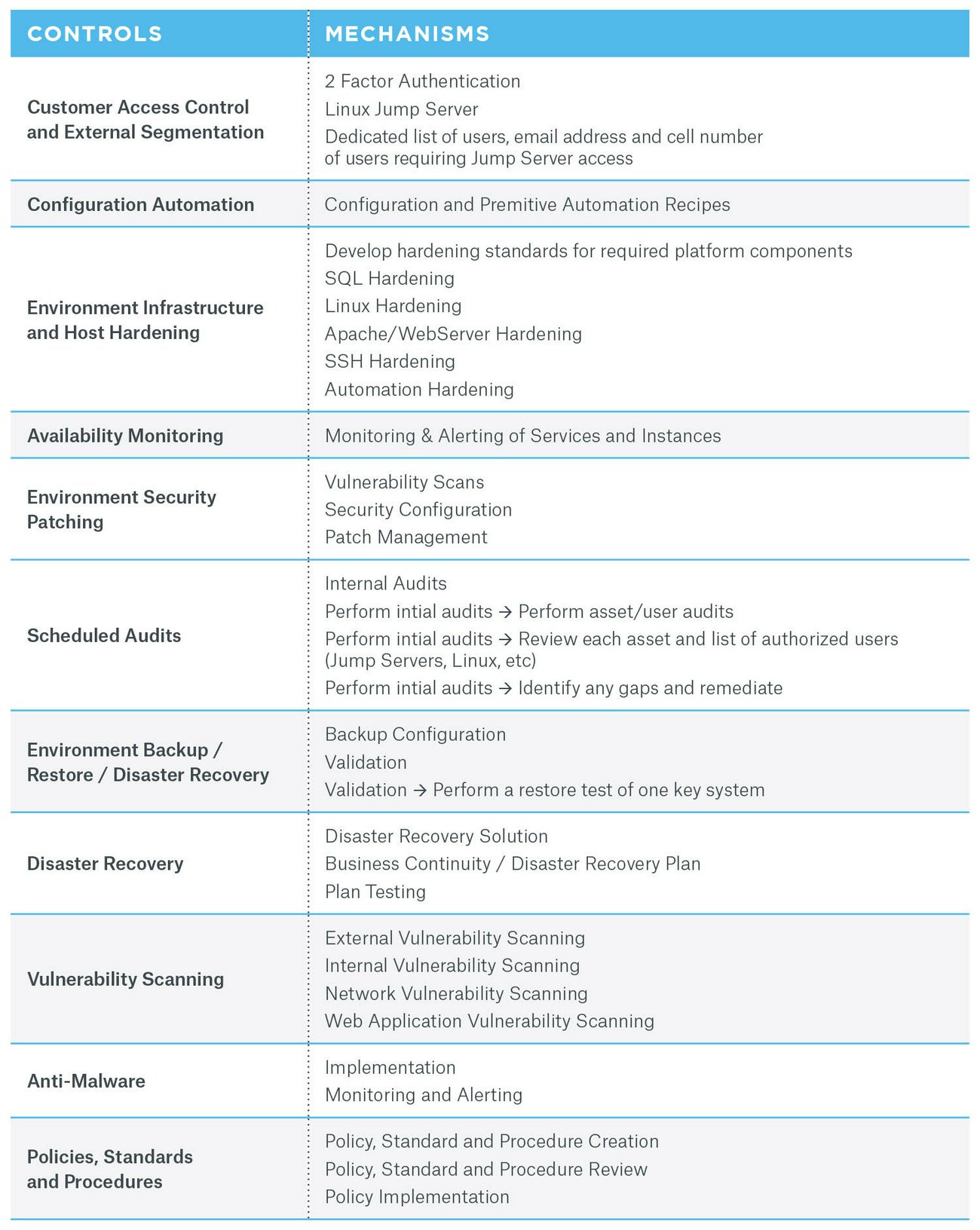
Email CloudOps at info@cloudops.com for more information, or download our white paper to learn about securing SaaS applications.
 RJ Stangle
RJ Stangle
RJ is a Partner and Managing Director at Securis, a boutique cybersecurity services firm that serves clients in Canada, the US, and the UK. With twenty years of experience in software and technology services, RJ has led consulting, development, professional services, and operational teams. He and the Securis team help organizations improve their security capabilities to effectively manage risk, protect their digital assets, and meet the growing demands of industry standards and regulations. RJ is a guest contributor to CloudOps’ blog series.

