Use a Palo Alto Networks firewall with CloudStack

Today we added a setup guide to the official Apache CloudStack documentation for the new features we developed to integrate the Palo Alto Networks firewall into CloudStack as a service provider.
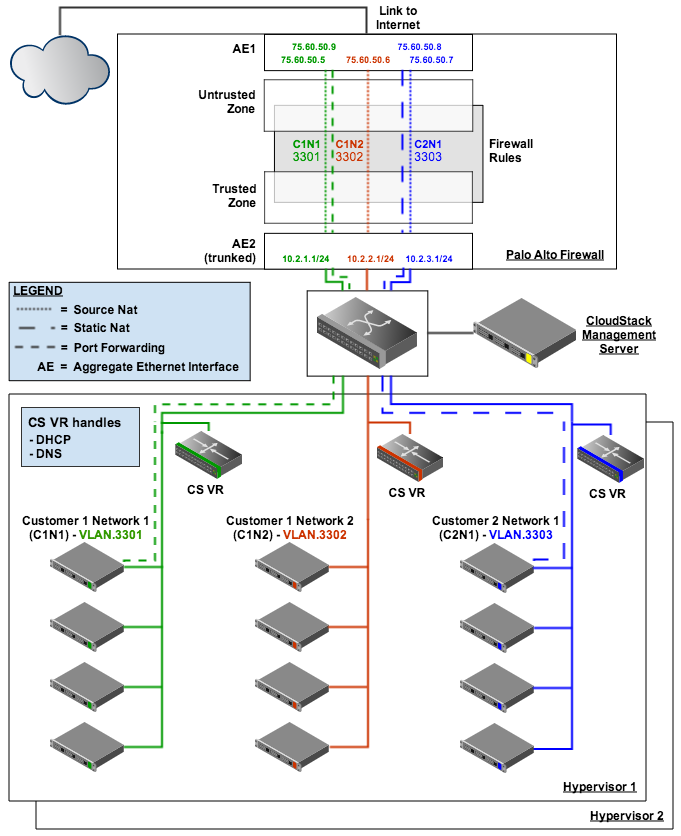
Start taking advantage of the Palo Alto Networks firewall orchestration in CloudStack by following the simple setup guide. Once the initial setup is done, CloudStack takes over and does all of the orchestration of the firewall.
This integration supports the following features:
Source NAT Management
Manage the Source NAT IPs
Manage the private gateway of the guest networks
Manage the Source NAT rules
Firewall rule management
Supports both Ingress and Egress firewall rules
Supports both ‘Allow’ and ‘Deny’ default Egress rules
Static NAT management
Port Forwarding management
Public IP provisioning
Guest network isolation
Threat Profile management
Log Forwarding management
In addition to the standard features that CloudStack offers, this integration also adds two additional features to take advantage of the unique power of the Palo Alto Networks firewall. The ability to add a Threat Profile and/or a Log Forwarding profile to all the allow firewall rules configured on the device makes this integration special. One of the main issues with the built in CloudStack virtual router is the fact that you have absolutely no visibility into the traffic flowing over your network. The addition of the Threat Profile gives you a lot more visibility into your network’s traffic and allows you to easily detect malicious behavior. The Log Forwarding functionality gives you a lot of flexibility in consuming the logs generated by the firewall so you can stay in the loop.
We are very excited to be able to offer this functionality and make it available to the community. If you have questions, please feel free to reach out to us.
